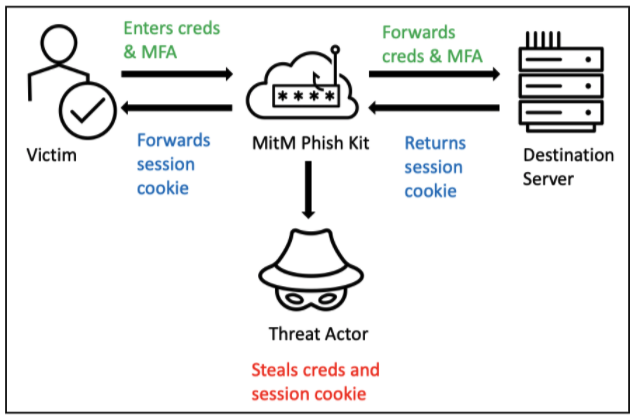
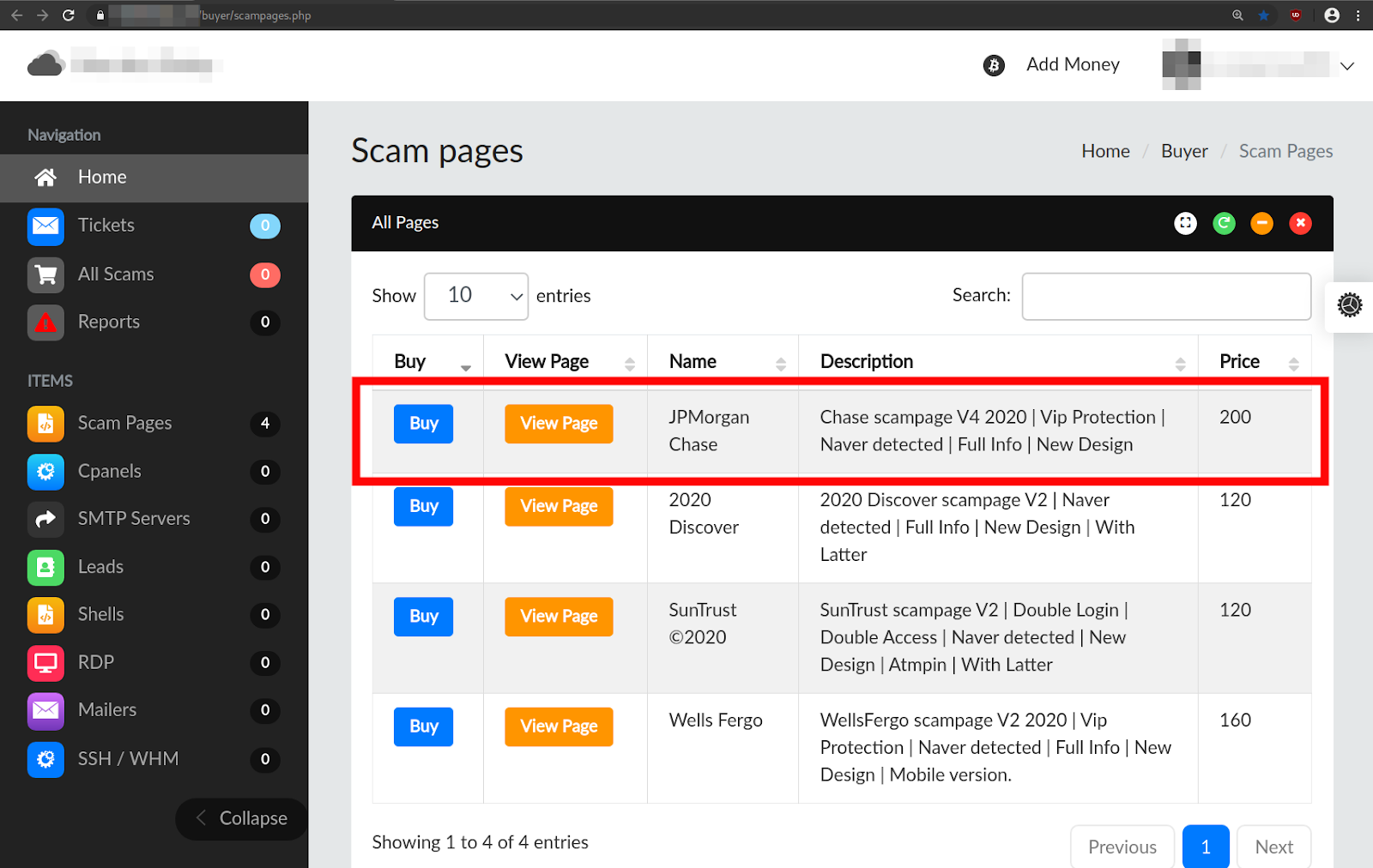
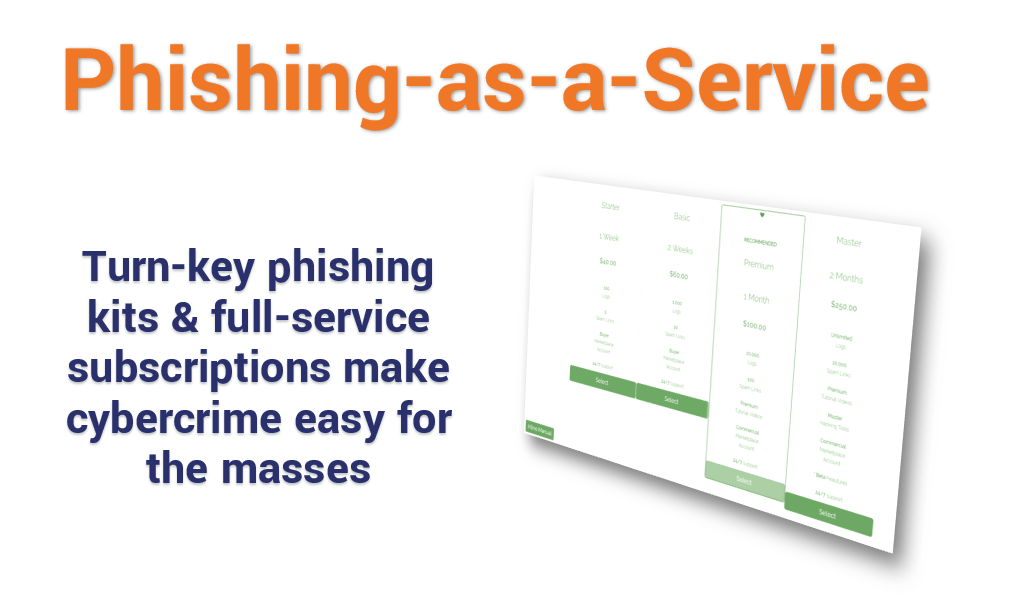
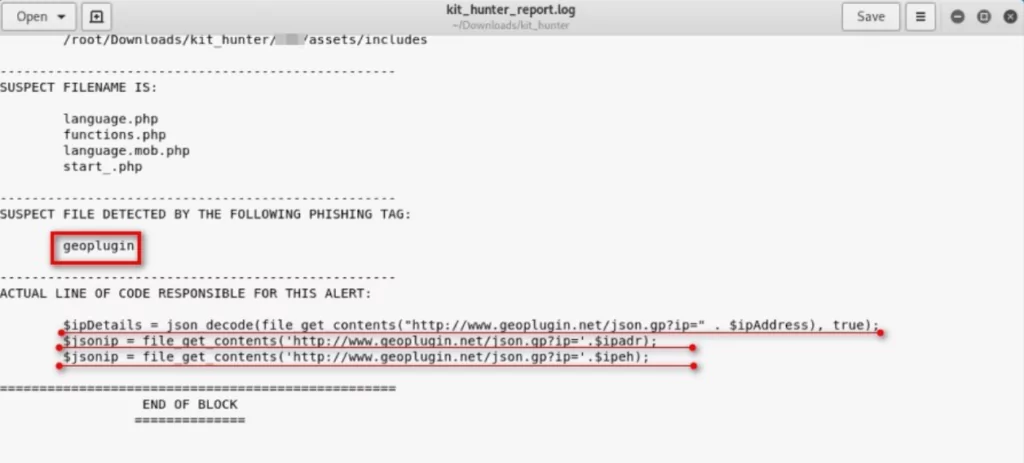
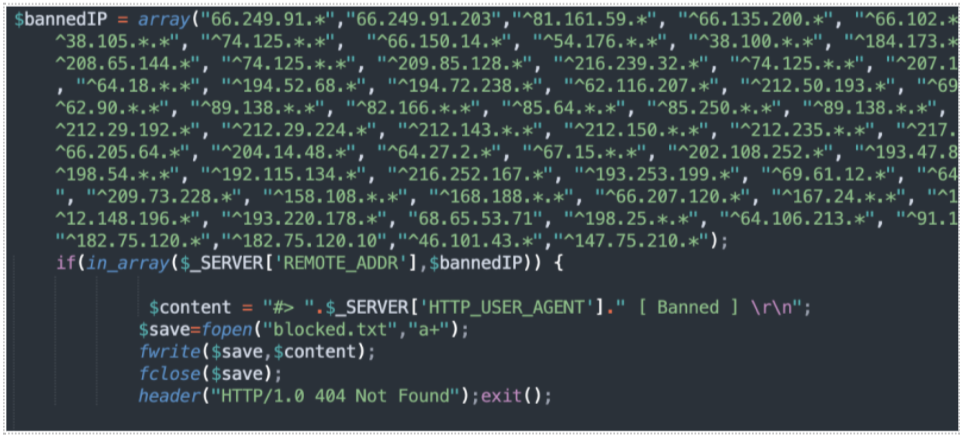
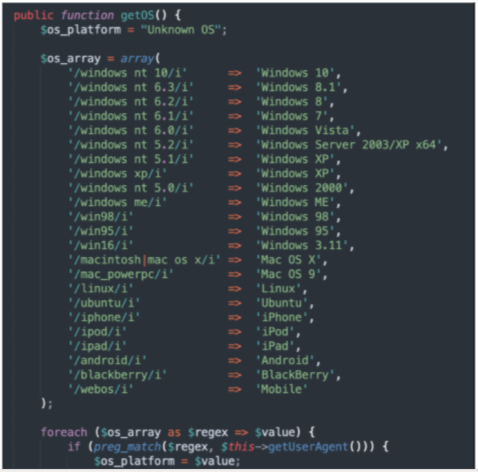
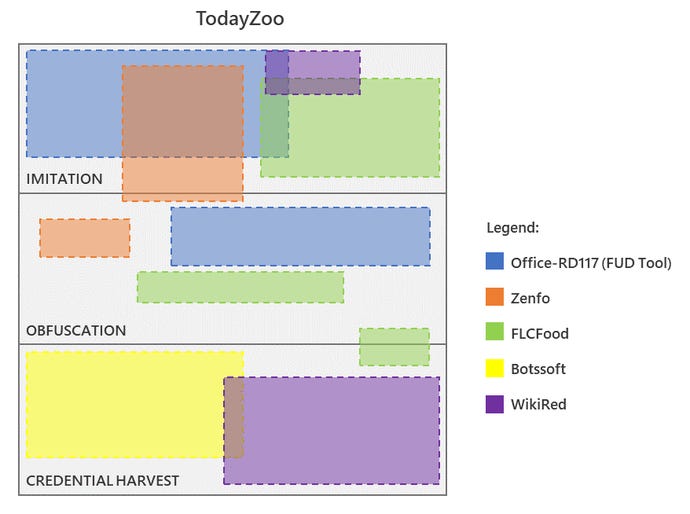
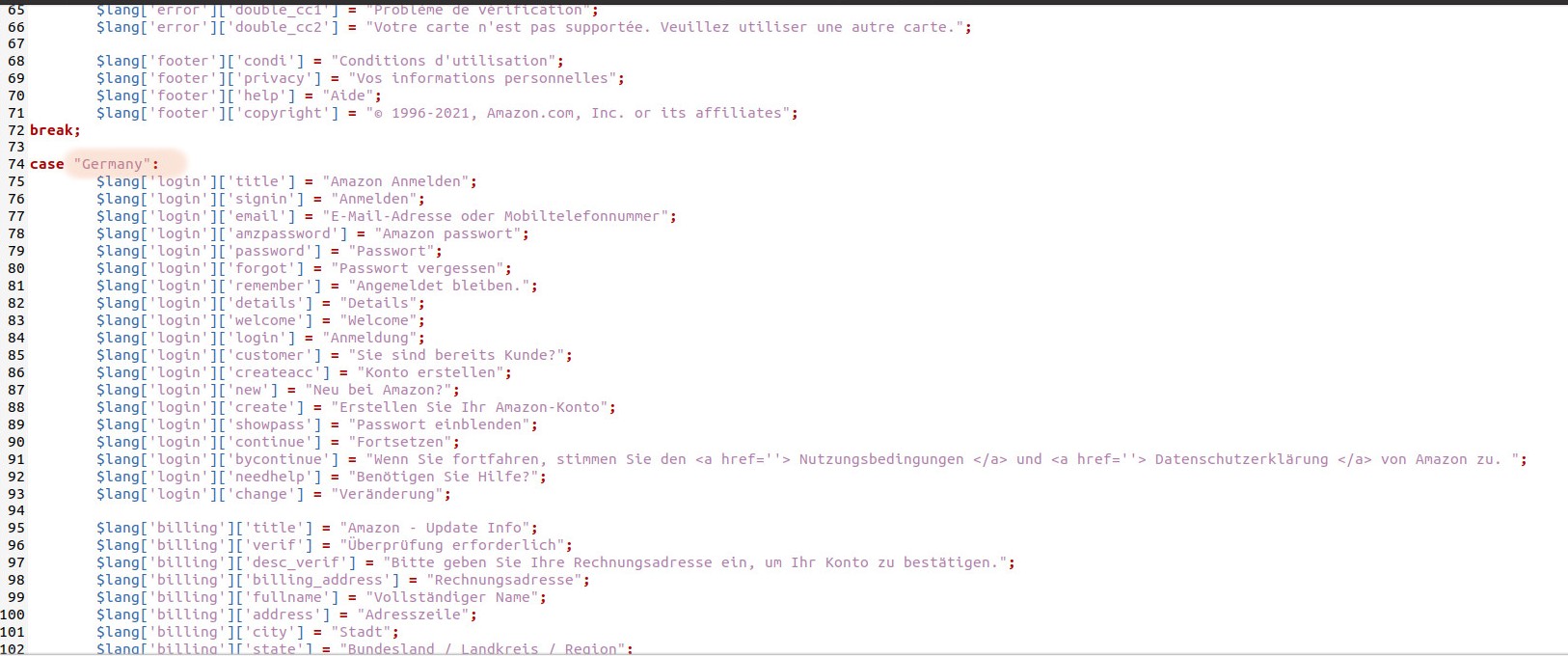
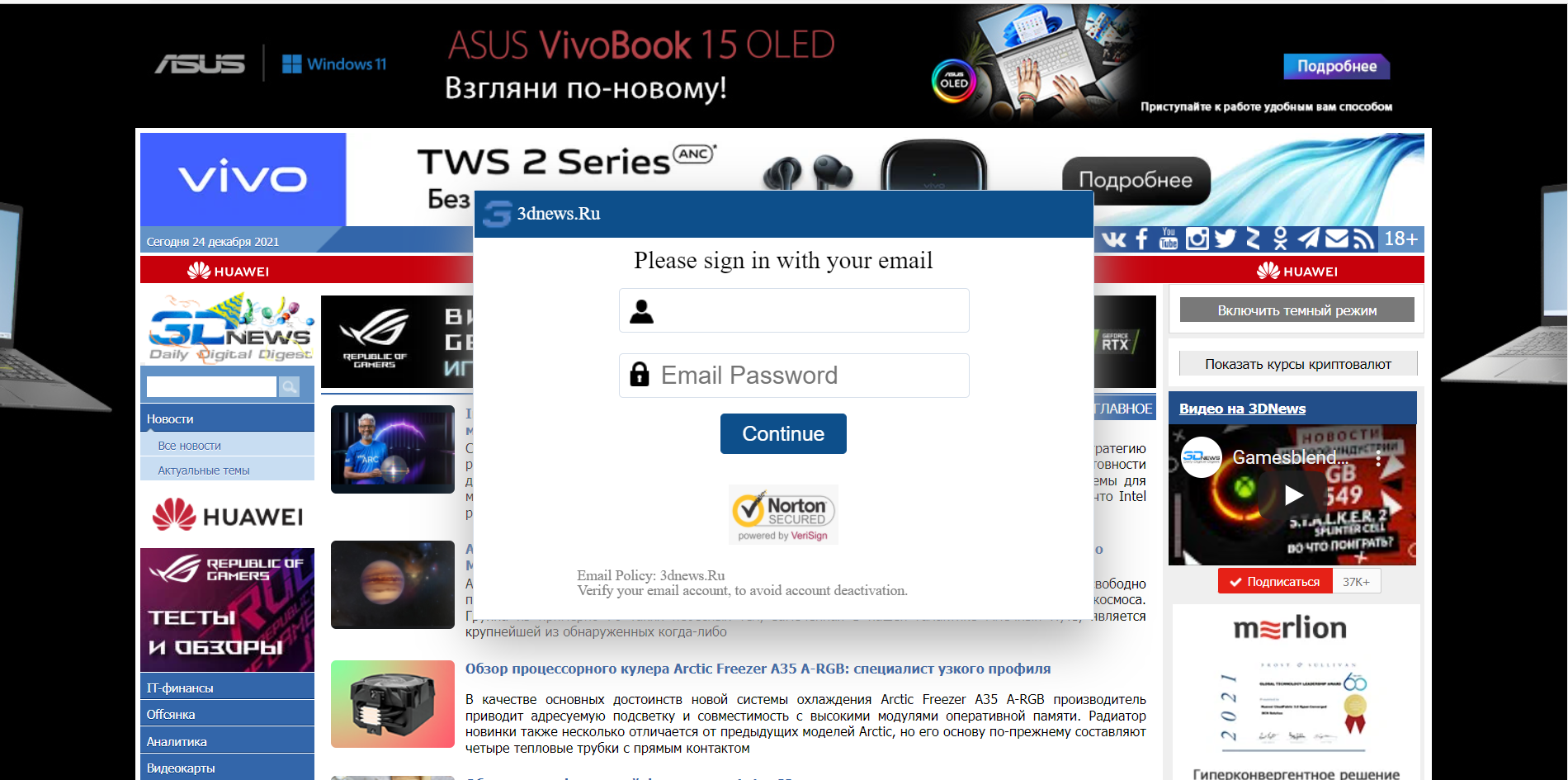
Phishing kit, per “automatizzare” le frodi informatiche: cosa sono e come proteggersi - Cyber Security 360

Group-IB: the use of phishing kits surges by 25% in 2022 as they become more evasive and advanced | Group-IB
GitHub - phish-report/IOK: IOK (Indicator Of Kit) is an open source ruleset of phishing threat actor tools and tactics